Click on the User Settings under the User Settings icon next to log in:
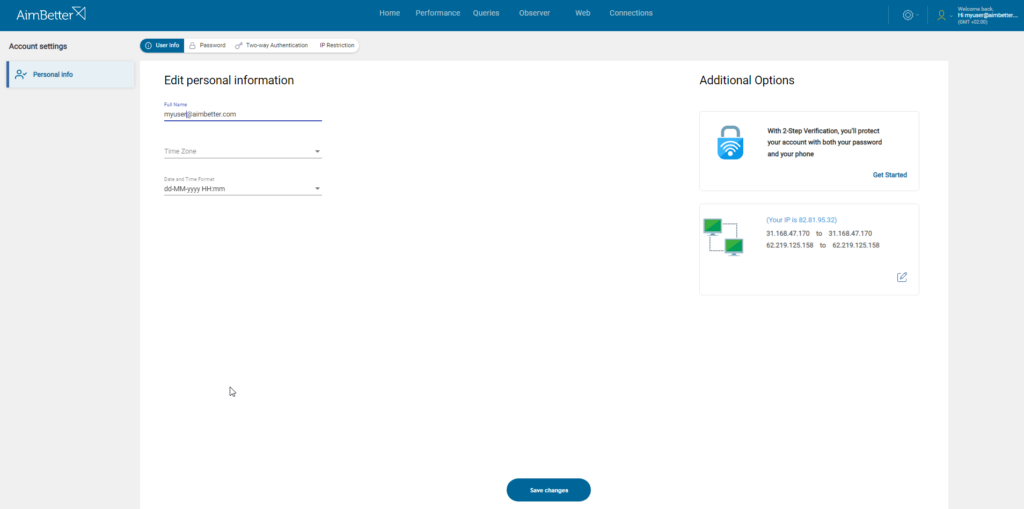
Personal Info
The User Settings is where the user’s personal information and security preferences are configured.
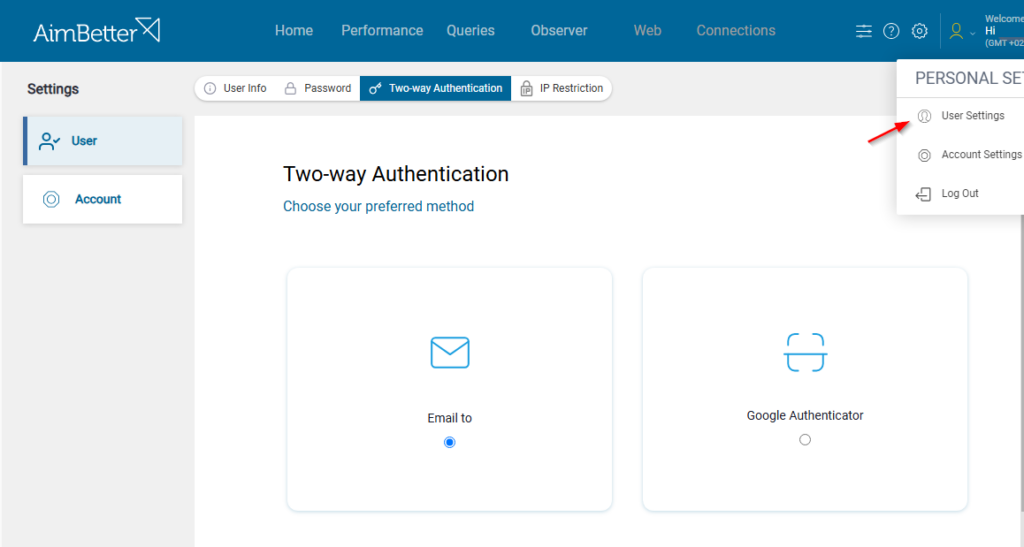
Two-Factor Authentication (2FA)
As part of our ongoing commitment to ensuring our customers’ data protection, the 2FA (Two-Factor Authentication) login is the default option for accessing the AimBetter system from July 2nd, 2023.
This method requires providing a code received by email or Google Authenticator after entering the user’s email during login. This procedure prevents users who are not part of the company from having access to the system.
To change the Two-way Authentication settings, click on the Two-Authentication tab.
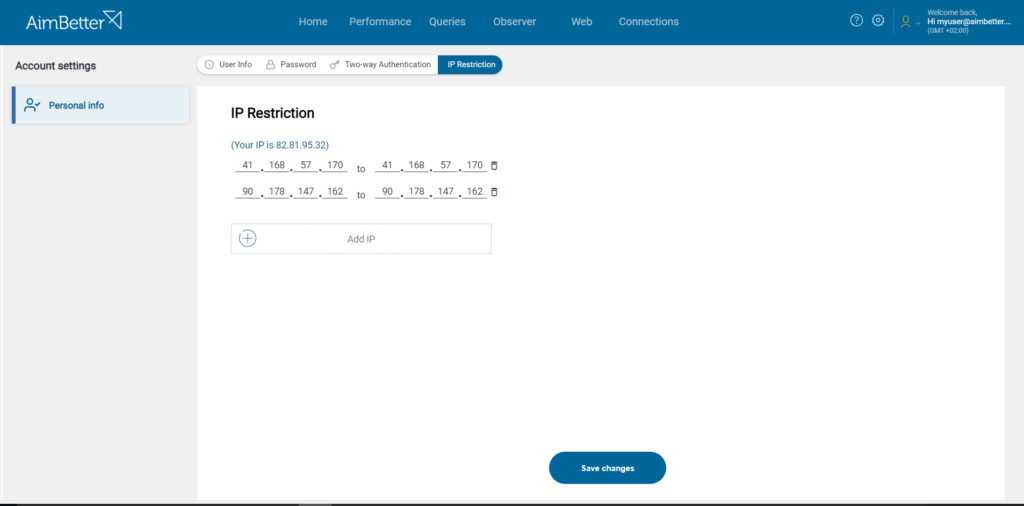
As a security measure, in case of disabling the default 2FA login, it is required that you restrict access to a specific IP.
IP Restriction
To change the IP Restriction settings, click on the IP Restriction tab.
You can check your IP address with your system administrator or through this link.
SSO – SAML 2.0
To configure SSO—SAML 2.0 on AimBetter, check this link.

 +1 (650) 449-8622
+1 (650) 449-8622